142 results found
SolutionLab
MDR&SOC
With our security team, the client can get Managed Technologies Services for Network and End-Point...
Whalebone
DNS4GOV
DNS4GOV is a government-oriented initiative to implement large-scale centralised protection for GOV...
NRD Cyber Security
CyberSet
CyberSet is a services automation toolkit for CSIRTs or SOCs. It works as a set of technologies and...
Sagenso
Telescope
Telescope, is an automated cybersecurity audit tool that evaluates a company's existing security...
Malizen
Malizen
Experience streamlined security data analytics with Malizen, a no-code interface that connects all...
Cryptomage
Cryptomage Cyber Eye
Cryptomage Cyber Eye™ Network Detection and Response-class network probe is much more than a simple...
Secure Practice
PrepJam by Secure Practice
Secure Practice is the European leader in cybersecurity awareness and preparedness. Kickstart your...
Safetech Innovations
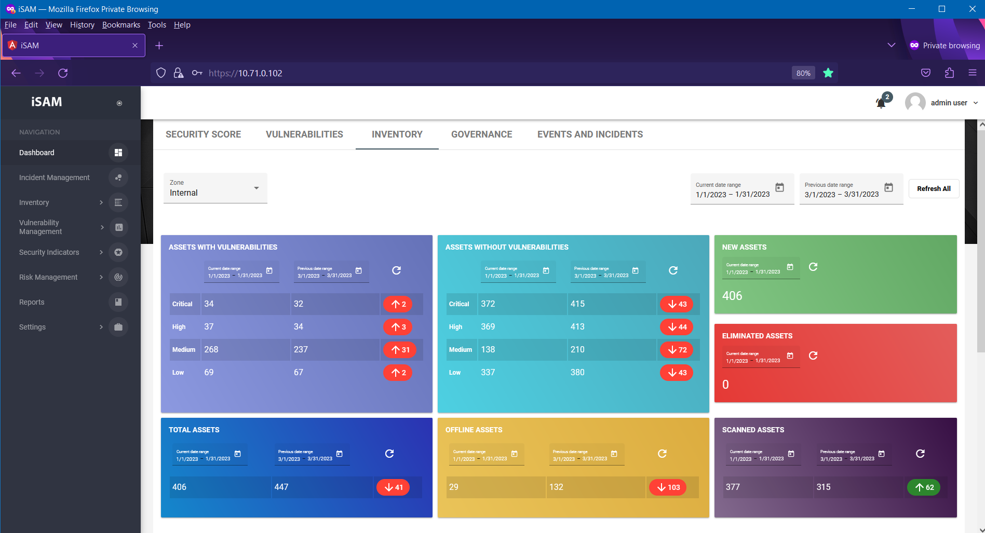
iSAM - Information Security Automation Manager
iSAM is a product developed by Safetech Innovations, in order to ensure automation in the...
WithSecure
WithSecure Elements XDR
WithSecure Elements Extended Detection and Response (XDR) is a unified solution, designed to protect...
SYSTANCIA
cyberelements
cyberelements is the cybersecurity platform for business performance. It is the only Zero Trust SaaS...
CyberDesk
Identity-Centric Data Security
CyberDesk helps you to adaptively control who can perform what actions with what data. Covering both...
Cyberday
Cyberday
Framework-Based Cybersecurity Cyberday offers a framework-based approach to cyber security...