142 results found
Atos Group
AI-Driven Managed Detection and Response
Atos's MDR service is a next-gen cybersecurity solution that leverages AI and cybersecurity mesh to...
Whalebone
DNS4GOV
DNS4GOV is a government-oriented initiative to implement large-scale centralised protection for GOV...
WithSecure
WithSecure Elements XDR
WithSecure Elements Extended Detection and Response (XDR) is a unified solution, designed to protect...
Wysam
Wysam
Wysam est une solution conçue pour les TPE et PME qui souhaitent sécuriser leurs échanges de données...
Secure Practice
PrepJam by Secure Practice
Secure Practice is the European leader in cybersecurity awareness and preparedness. Kickstart your...
CyberDesk
Identity-Centric Data Security
CyberDesk helps you to adaptively control who can perform what actions with what data. Covering both...
Safetech Innovations
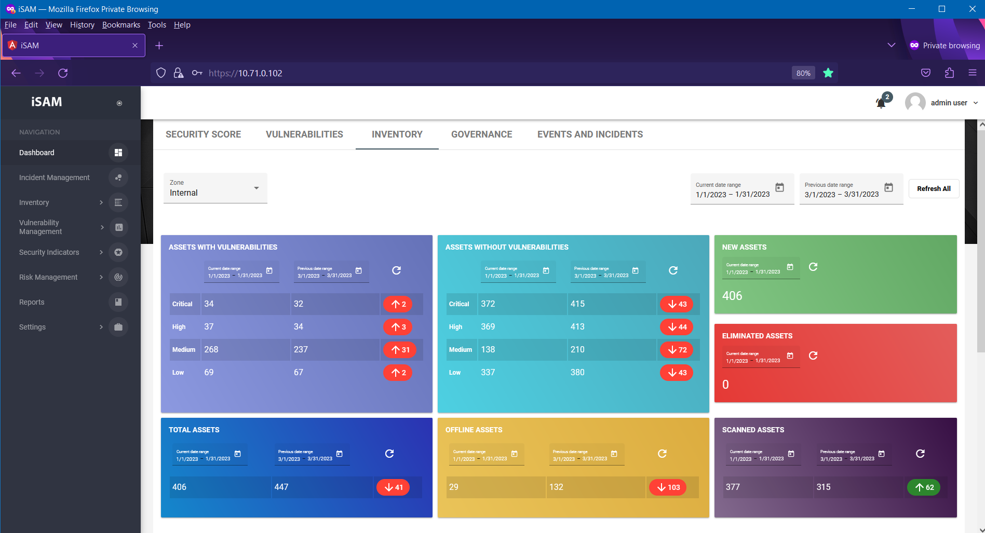
iSAM - Information Security Automation Manager
iSAM is a product developed by Safetech Innovations, in order to ensure automation in the...
Binalyze
Binalyze AIR
Binalyze AIR is an investigation and response automation platform powered by forensic-level...
Threema GmbH
Threema Work. The Secure Business Messenger
Threema Work is a secure and GDPR-compliant business communication solution that facilitates mobile...
Guardian360 B.V.
Demonstrate Compliance by securing your information
As a compliance officer, you face the challenge of complying with regulations such as GDPR and NIS2...
Modino.io
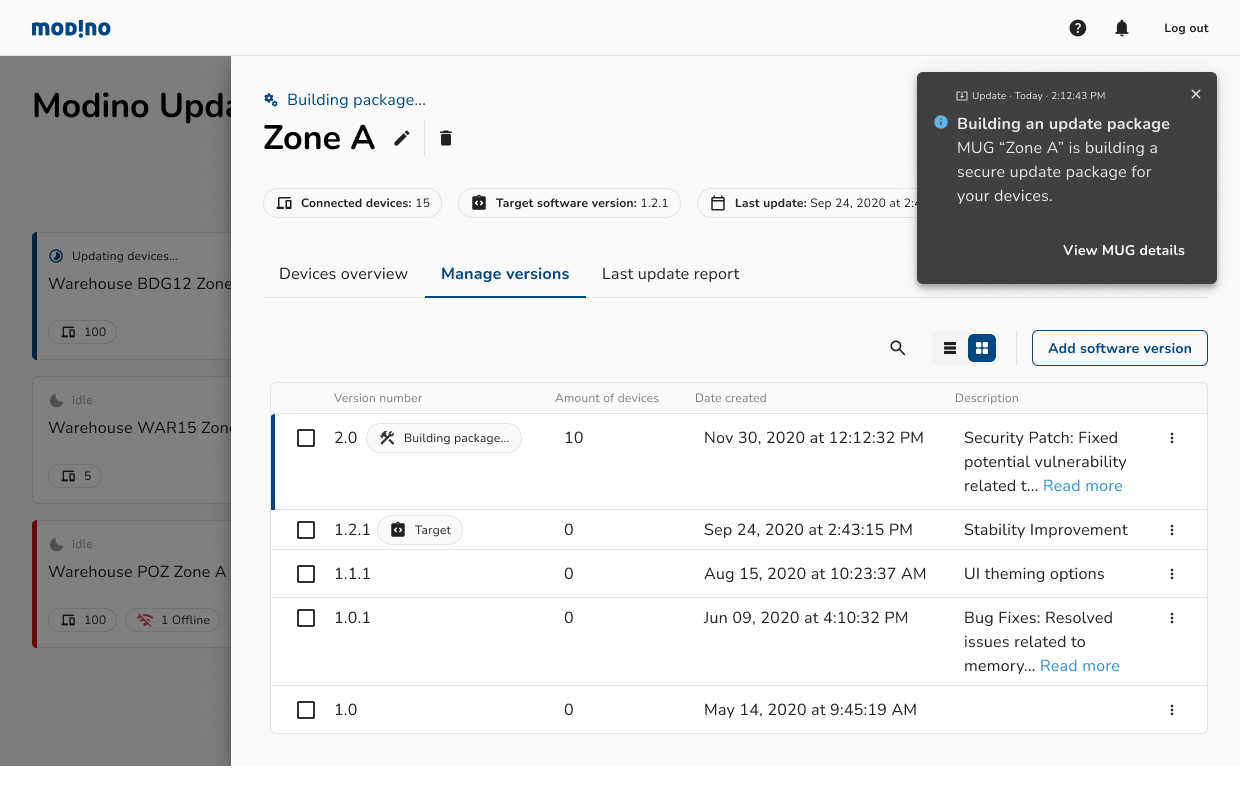
Modino.io - safe and secure digital artifacts delivery
Modino.io is an on-prem / cloud platform for performing safe and secure updates for: - IoT devices -...
Secfense
Secfense IdP (Identity Provider) | Secure, flexible and simplified identity management
Secfense IdP marks a significant advancement in cybersecurity, delivering unparalleled flexibility...